What goes into SOC 2 and HITRUST? (with Vanta)
Get Out-Of-Pocket in your email
Looking to hire the best talent in healthcare? Check out the OOP Talent Collective - where vetted candidates are looking for their next gig. Learn more here or check it out yourself.
 Hire from the Out-Of-Pocket talent collective
Hire from the Out-Of-Pocket talent collectiveIntro to Revenue Cycle Management: Fundamentals for Digital Health

Network Effects: Interoperability 101
.gif)
Featured Jobs
Finance Associate - Spark Advisors
- Spark Advisors helps seniors enroll in Medicare and understand their benefits by monitoring coverage, figuring out the right benefits, and deal with insurance issues. They're hiring a finance associate.
- firsthand is building technology and services to dramatically change the lives of those with serious mental illness who have fallen through the gaps in the safety net. They are hiring a data engineer to build first of its kind infrastructure to empower their peer-led care team.
- J2 Health brings together best in class data and purpose built software to enable healthcare organizations to optimize provider network performance. They're hiring a data scientist.
Looking for a job in health tech? Check out the other awesome healthcare jobs on the job board + give your preferences to get alerted to new postings.
TL;DR
SOC 2 and HITRUST are common security frameworks that healthcare companies will inevitably end up encountering in their journey. Today we’ll walk through the differences between them, the process by which to get them, and the kinds of security measures you’ll need in place.
Vanta is a company that helps you gather and prepare the information you need in order to be compliant for these frameworks. We go through how they do this, including product screenshots!
Vanta is riding on cybersecurity as a priority in healthcare now and brings standardization, automation, and integrations to speed up the process. We discuss some of the difficult parts of building in this space, including competition + the evolving philosophies around security and compliance.
We’ve also managed to convince the Vanta team to give OOP readers $1,000 off (through this link). Mama look at us, we’re negotiating!!

This is a sponsored post - you can read more about my rules/thoughts on sponsored posts here. If you’re interested in having a sponsored post done, let us know here.
_______
Name Of The Company - Vanta
Vanta…you’ve probably seen the ads, the puns about SOC 2, trust management, etc. You have to understand - for a newsletter writer, getting a Vanta sponsorship is a rite of passage, a sign that you might have actually made it in the world. Like when Youtubers get a “Manscaped” or a VPN sponsor.

What’s the Pain Point Being Solved? SOC 2 and HITRUST Basics
A mistake that people new to healthcare make is that they do not get their compliance stuff in order early. This ends up biting them in the ass later when they start landing their first large clients that require HIPAA compliance, SOC 2 compliance, or HITRUST certification. If you haven’t gotten your house in order, then you have to do a lot of stuff retrospectively which can delay deals significantly.
Today, I’d like to explain the basics of SOC 2 and HITRUST so you’re at least aware of them. At a high-level, both are frameworks to ensure you have your security in order. They typically look at “controls” - the policies, procedures, and technical thingamajigs to make sure you’re secure.
SOC 2 Overview
SOC 2 is a voluntary compliance standard developed by the AICPA (American Institute of Certified Public Accountants), NOT a law or healthcare-specific regulation. SOC 2s result in an attestation report demonstrating that your organization meets industry-defined security controls.
SOC 2 focuses on up to five “Trust Services Criteria” (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. But it’s like the Jackson 5; one is a little bit more important than the others. Security is the mandatory criteria, while the others are added based on your business and compliance objectives.
Here are a handful of examples on the security front, but there are many more:
- Making sure only the right people can access sensitive data. E.g. EHR integration engineers get read-only access to PHI tables, and the finance team can’t touch this (feat. MC Hammer).
- Logging and monitoring so you can see who did what, where, and alert you if it’s suspicious. If someone is doing a patient-data export > 100 MB at 2 a.m. from an unknown IP in Bangladesh, you…should probably get a notification.
- Encryption in transit: Don’t store your stuff in plain-text! This is for you, vibe coders! You need to transmit data through Transport Layer Security (TLS) protocols to encrypt it.
So how does this actually get evaluated? Typically what a process looks like is this:
First, you’ll likely pick between getting a SOC 2 Type 1 or Type 2 report, which has diabetic vibes. This is typically the starting point for most companies. Type I typically focuses on what your security control looks like at a point in time, and is usually a good “stepping stone” before going for Type II.
You’ll start by getting an assessment of your security gaps you need to patch up. Companies like Vanta have a SOC 2 control list to start. Or, you can review the criteria and develop controls yourself, with an external assessor coming in and finding the gaps. This will give you a plan on what needs to be fixed, who’s running point on it, etc. Congrats, you’re on the road to SOC tuah securin’ that thang (kill me).
Once you’ve made those fixes, you’ll look for an auditor to actually check them. This is done by an independent party that is an accredited Certified Public Accountant. Why an accountant does this is beyond me, maybe they’re good for security because they’re such serious people.
Once the auditor is done they’ll give you a report, which you can show your customers/whoever asks when they want to know if you’re SOC compliant. However, getting a Type 1 report is a point in time assessment and usually a way to show them you’re in the process of getting a Type 2 report. It’s the “trust me bro” report, it’s not enough on its own.
While a Type 1 shows that you have the processes in place, the Type 2 report demonstrates that you actually abided by it over time. During a Type 2 report an auditor is observing the company over a window of time (usually at least 3 months for your first Type 2, with between every 6 months and 1 year for reports going forward) and seeing whether the policies are actually being followed. The auditor might ask to see logs of different software, have you run through a scenario to see what your company has set up, take a sampling of employees and see if they have background checks and training completed, etc. It’s like a colonoscopy, but for your security butt.
The auditor will produce a report at the end that gives their opinion about how you did on the different security controls, including whether there was a deviation in your control’s operation, or an exception and what it was. Just FYI: you typically know an exception is being noted ahead of the report generation, and you’re given an opportunity to explain it + provide remediation steps you’ll take to close the gap. You can see an example/outline here.
HITRUST at a HILEVEL
HITRUST is the Health Information Trust Alliance…healthcare acronyms like to be on the nose. HITRUST is a more healthcare specific security framework and takes the greatest hits from the many different security standards that healthcare companies will typically encounter like HIPAA, NIST, ISO 27001, PCI, and other capitalized letters that sound like loud noises.

There are three different levels to go from easy to hard and increasingly more required controls + longer observation periods - e1 is the lowest, i1 is intermediate, and r2 is “Through the Fire and Flames on expert” difficulty. Many times, a company will get the e1 certification and show customers that they’re en route to getting the others.
First, you pick which level you want to go for based on whether your customer is demanding it + what you can actually do. Companies optionally can hire an approved assessor to perform a Readiness Assessment to look at your environment, identify gaps, and make a remediation plan. Automated compliance companies like Vanta will also do this via integrations, and map to the HITRUST MyCSF tool to scope your applicable controls and generate a gap assessment.
Then, you’ll need to actually implement the required controls, policies, and procedures to meet the standards for certifications and fix your shit. The person that checks your compliance is not just anyone, but a firm specifically approved as an external assessor for HITRUST. All this data needs to be pumped into MyCSF. If you meet all the requirements, then you’ll get a HITRUST certification for the level you target.
Below are ball park timelines though they’re highly based on the type of data, the systems involved with that data, people, and locations.
e1
- Readiness: 1-2 months
- Validated Assessment: 90 days
- HITRUST QA: 1-2 months
i1
- Readiness: 4-6 months
- Validated Assessment: 90 days
- HITRUST QA: 2+ months
r2
- Readiness: 6+ months
- Validated Assessment: 90 days
- HITRUST QA: 2+ months
That’s the short version, but you can read the longer version of what HITRUST is and what you need here.
SOC 2, HITRUST - Differences, Similarities, and Costs
SOC 2 and HITRUST have some overlap, differences, and ideological splits.
At a high level, both of these frameworks are about seeing if your internal processes yield a secure company. Neither of them are laws, they’re things your customers typically want to see. They follow similar processes in terms of how they get scoped and graded. And you’re very likely to implement controls that work across the two frameworks (e.g. how you handle personal health information).
There are a few major differences between the two. For one, SOC 2 is graded more on a set of “principles” of what security looks like, and they look to see what kinds of processes/controls you have in place that line up to those principles. This gives auditors a bit of flexibility in judging how well your company meets these principles. That’s also why the end report of a SOC 2 audit is a letter/attestation, which is basically a professional opinion of your compliance. But it’s also a framework that is intentionally flexible because it works across a lot of different types of companies.
HITRUST was originally focused on healthcare, though its frameworks have evolved to incorporate over 60 different standards. They’re also more prescriptive about WHICH controls organizations are expected to implement.
For example: SOC 2 might look at a principle of “logical management” and give you a positive opinion if you use Yubikey, track who’s accessing what, etc; but gives you some flexibility of choice in how you handle system access. HITRUST, however, is specific about mandating multi-factor authentication, which could include methods like biometrics or a hardware token for any sensitive system and it’s a “yes or no” (whether you did it). Also, HITRUST itself updates which controls you need to have every year; it’s not up to the companies.
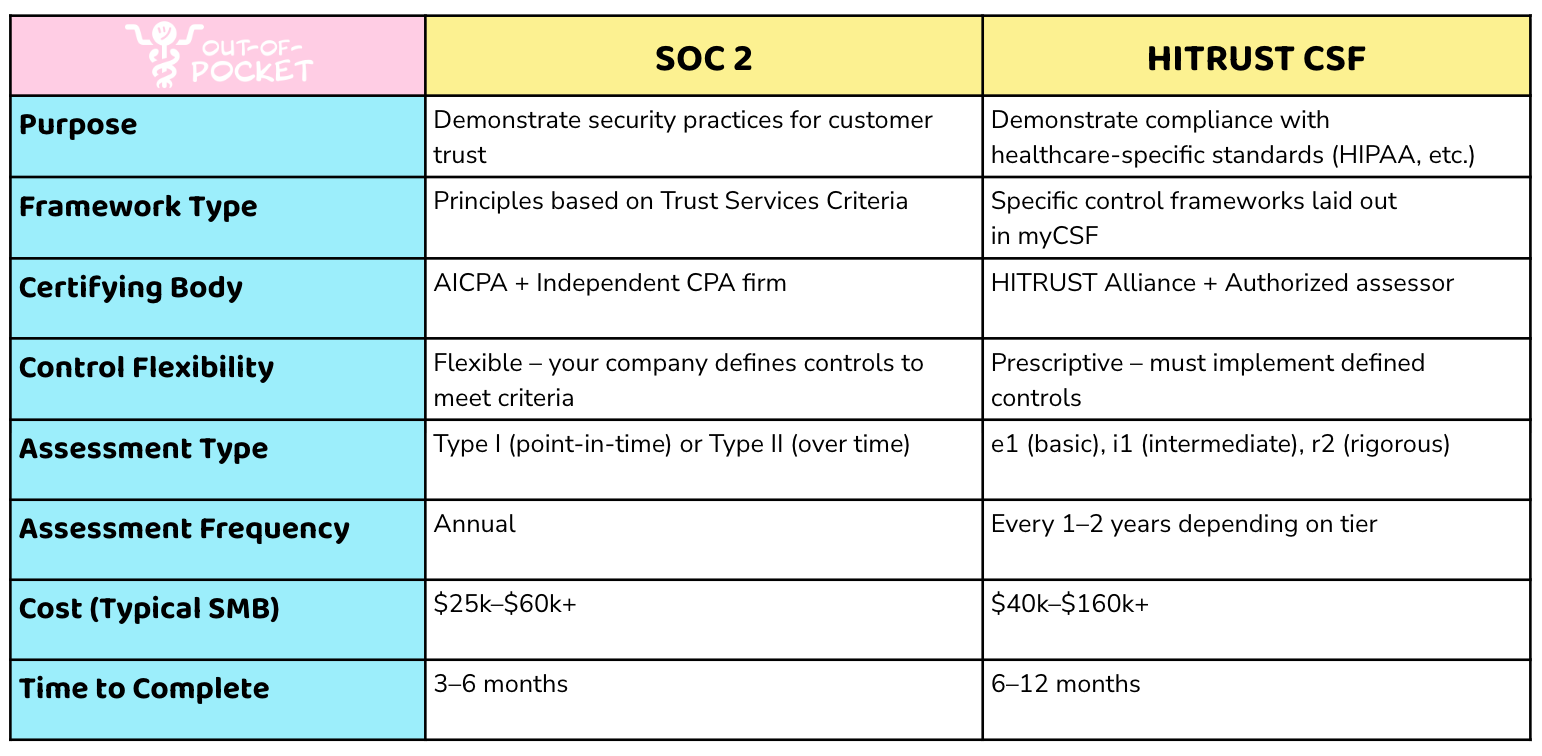
The end result of HITRUST is an actual certification that’s pass/fail. It’s a much higher bar to meet and takes significantly more time/internal resources to be compliant. Companies generally start with SOC 2 and HIPAA compliance first, but most enterprise healthcare customers will expect HITRUST certification or a clear path to getting it before they work with you.
What does Vanta do? What pain point do they solve?
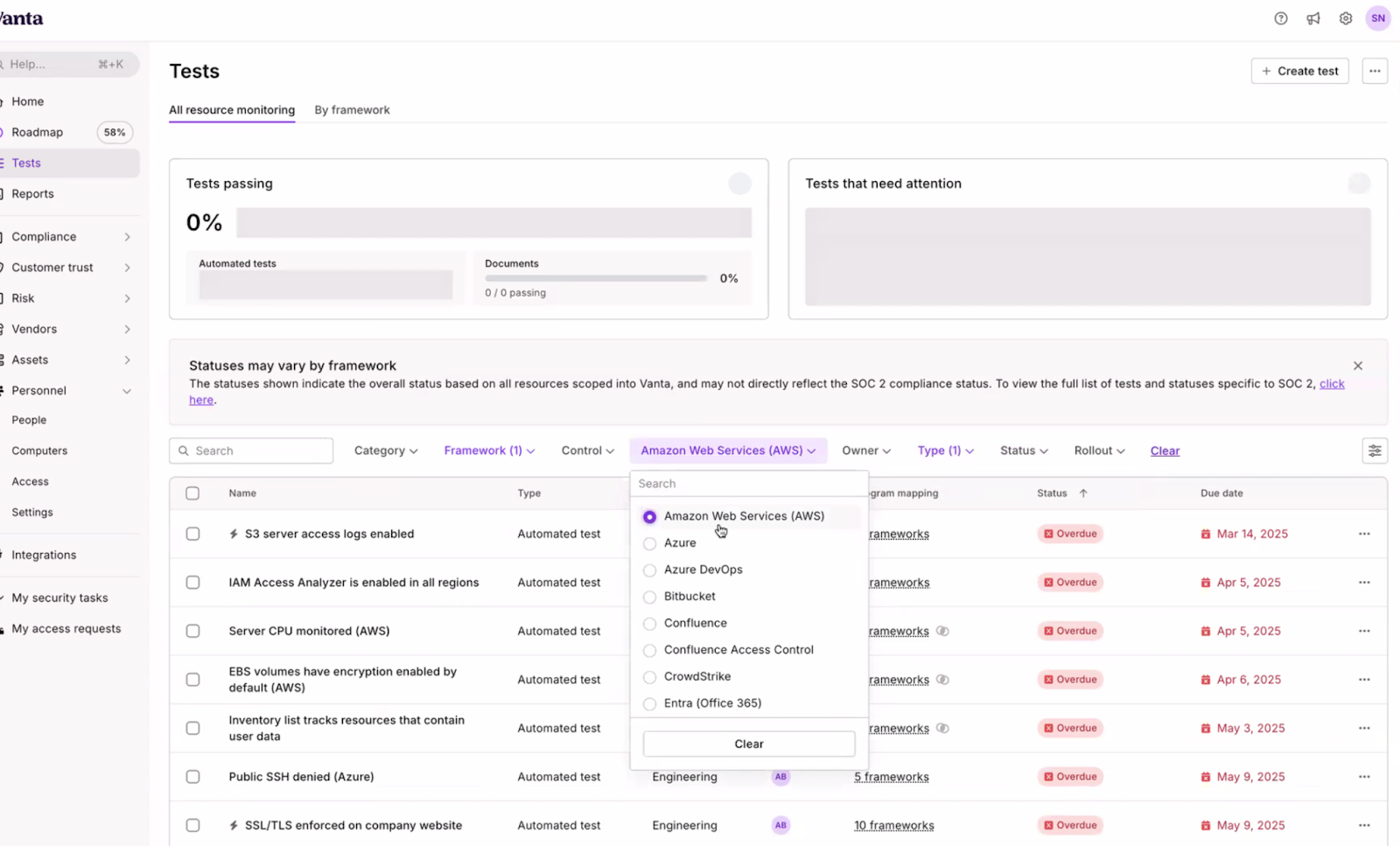
Vanta has a bunch of integrations that connect directly to the systems you already run like AWS, Google Workspace, Okta, GitHub, your HR system, etc. One benefit of this is that the integrations passively collect the info you need for an audit, and another is that compliance monitoring becomes continuous instead of “snapshot in time”. This speeds up the time to become compliant + require less personnel hours to manually gather this.
They also give you suggested security things you should do to meet the requirements for any of the security frameworks you choose (SOC 2, HIPAA, and HITRUST being the most relevant for healthcare companies). For SOC 2, for example, it’ll pull the live, continuous data coming from the different parts of your tech stack to do things like:
- Make sure multifactor authentication is enforced
- Check that encryption is enabled for every storage bucket
- Timestamp and ensure that critical vulnerabilities are patched within defined timeframes
- Check that off-boarded employees no longer have active accounts
- Many more to meet the other controls
There’s also a lot of documents you’ll need to upload for compliance. Vanta gives editable policy templates, lets you assign any human tasks (like quarterly access reviews) to the right people, and maintains an evidence repository for your auditor. Then your auditor can just view the controls, tests, and timestamps through Vanta’s audit portal instead of requesting screenshots or spreadsheets.
HITRUST is similar, but Vanta can set up continuous data feeds onto the HITRUST CSF’s and map them to the required controls they’re looking for. They can also cross-map evidence that overlap with requirements for SOC 2, and then flag the additional items unique to HITRUST. Vanta tracks completion of these tasks and stores the necessary evidence artifacts such as policies, third-party/ risk assessments, automated test data, and other document requests required for each of the HITRUST levels.
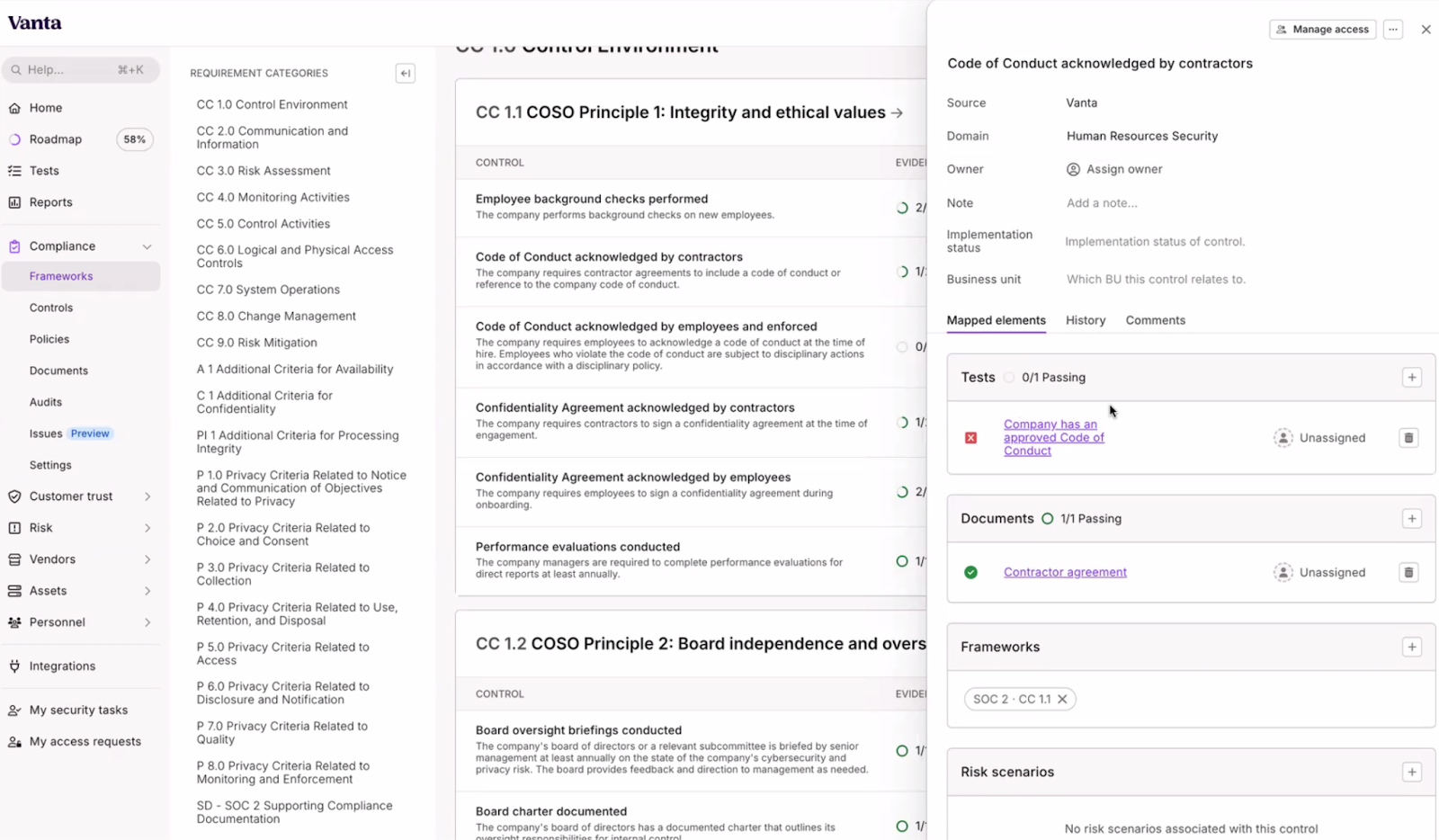
With the company features and data in one place, they can do a few other things, too:
- They have a Trust Center that lets you create an external page of your SOC 2 Reports, HITRUST certification, and other security things a company might ask about. You can see an example of LeanTaaS’s page here.
- They use AI to automate filling out security questionnaires companies have. If you’re receiving SOC 2 reports, Vanta’s AI can help analyze them to understand a company’s strengths and weaknesses.
- They can create risk scores within your organization to tell you where you need to beef up. They have a vendor risk management tool that looks at the vendors YOU use and provides you AI-based mechanisms to rapidly review their documentation and assess their risk.
What Is The Business Model And Who Is The End User?
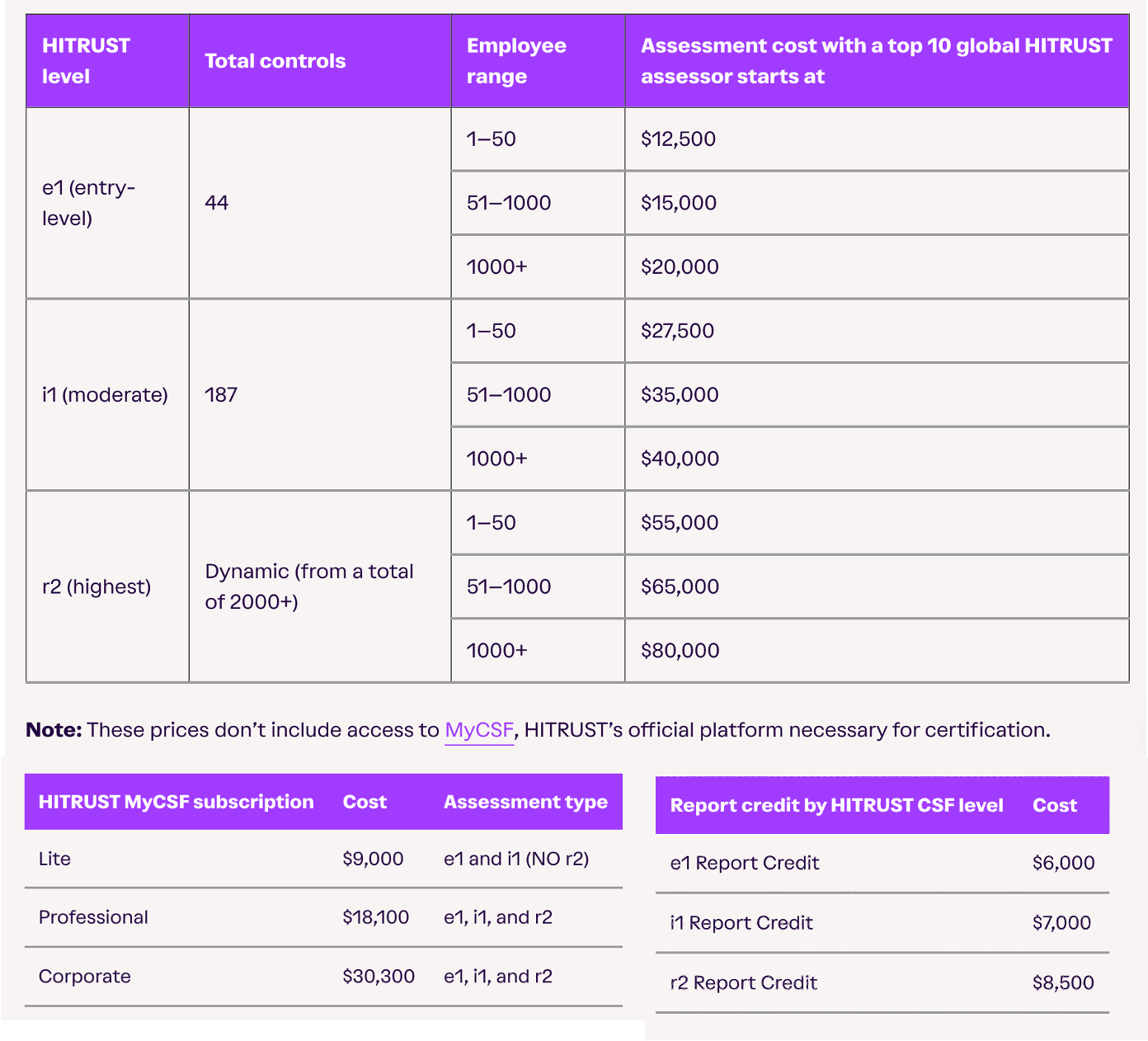
At a high level, SOC 2 is anywhere between $10K-15K for smaller companies and way more for larger companies. HITRUST has several mandatory fees you need to pay to access myCSF and then assessment costs on top of that (you can see some tiers below).
Vanta charges B2B SaaS fees that scale depending on a few different things. You can see the full list here, but it feels like a waste in an already long newsletter to rehash what’s written there in detail. At a high level:
- Core/Plus - Gives one framework, automated evidence capture, policy templates, light Trust Center
- Growth - Gives you custom controls, risk register, 144 AI-answered questionnaires/year
- Scale - Gives you 288 questionnaires, multi-workspace support, deeper role-based access controls, and an API
- Enterprise gives you white glove support, custom frameworks, and anything money can buy (compliance wise)
Most people at the company will end up being part of the compliance process, but getting the company ready usually falls on one person/team. Depending on the size of the company, this can be an unfortunate engineer who “volunteers” for “career growth” purposes or your internal DevOps/Compliance department (who definitely didn't need more work).
Job Openings
Vanta is hiring for lots of different roles in sales, engineer, people ops, general minions, etc. which you can see here.
Out-Of-Pocket Take
A few things I like about Vanta:
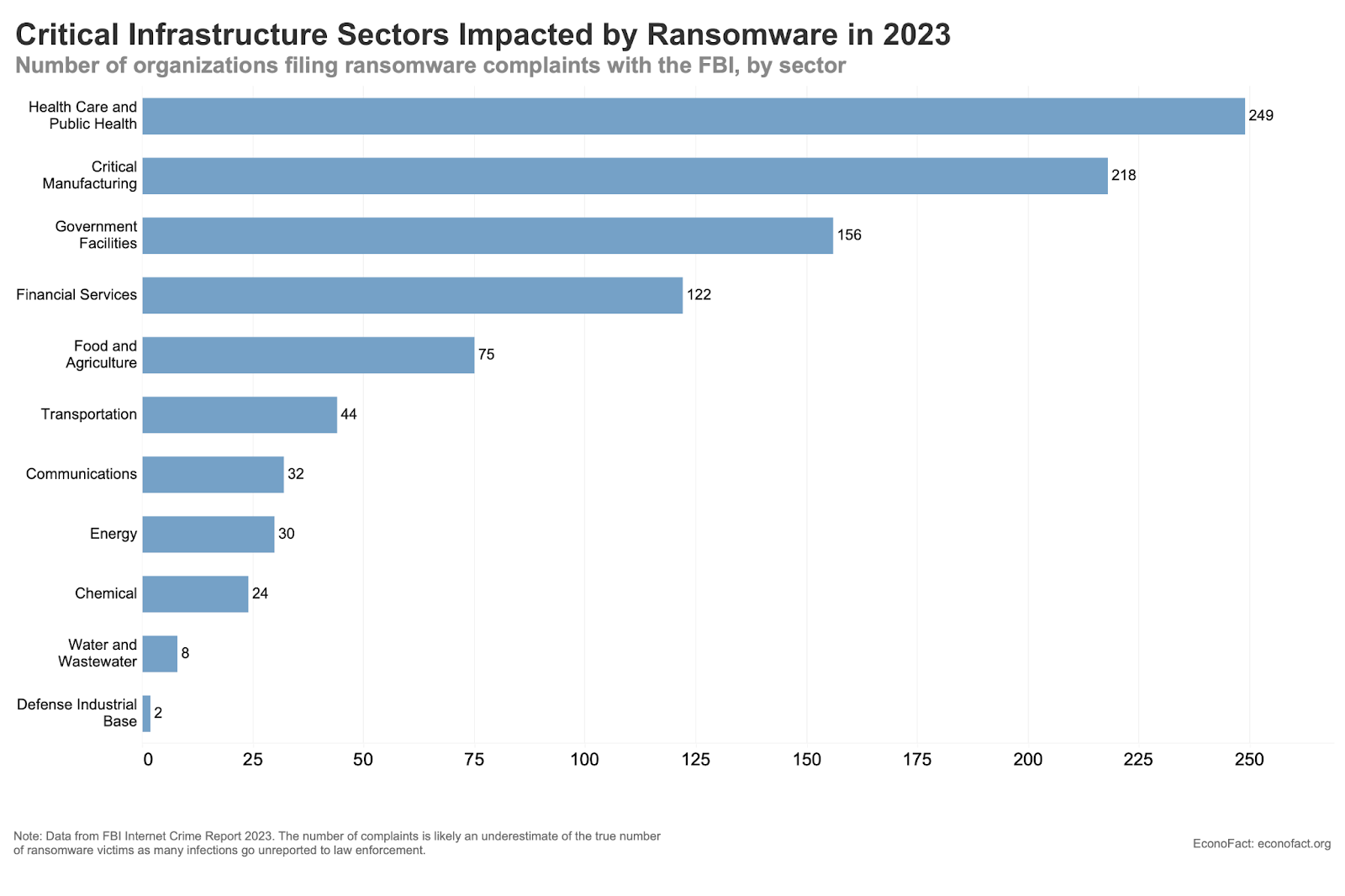
Security is becoming a priority in healthcare with $ at stake - One thing I learned while talking to people about this topic is that cyber insurance premiums are going up considerably in healthcare + enough hospitals have experienced lost revenue due to ransomware attacks. The cybersecurity incidents are now hitting profit & loss statements in a material enough way that they need to address it.
On top of that, the Change Healthcare breach made everyone hyperaware of how interconnected their vendors are, which means that enterprises are asking for more security requirements upfront from companies they work with. Vanta is trying to ride this wave by making it easier to fulfill those requirements.
Speed - It’s hard to stress how annoying it is for compliance to be the thing that holds a deal up. Anyone that’s been in healthcare long enough can tell you that the longer a deal drags out, the more time there is for someone to say no or some strategic shift at your buyer kills the whole deal.
Compliance lives in the background of the sales cycle the whole time, the spectre you don’t want to think about. Usually companies will continue with the sales process while you’re getting your SOC 2/HITRUST done, but you absolutely do not want the deal to be held up because you were slow on the compliance front. Vanta focuses on speed to compliance, because nothing is worse than a deal getting dragged out because there are open security questions you need to fulfill.
The standardization and simplification of compliance - You could do this yourself if you wanted to. It would require coordinating with an external consultant to help you figure out what you need, sending a lot of PDFs/screenshots/excel sheets internally, and use a lot of internal personnel time on this. This newsletter is already fighting for its life in your inbox, you don’t want more emails in there to coordinate this.
While you’re still going to need quite a few personnel hours for this, it should be lower. There are a few different ways Vanta tries to achieve this:
- Automated evidence collection - 375+ integrations allow companies to capture the data they need passively instead of a person staying on top of it.
- Standardizing things - If you say you want to be SOC 2 compliant, Vanta can provide you the controls you’ll need. They have templates for certain documents/policies you need to fill complete, with guidance where applicable, automation incorporated throughout, etc.
- Self-serve - Customers can request your reports, certifications, etc. from the Trust Center so they don’t need to keep pinging your team to answer questions.
- Single workspace - You don’t have to coordinate through a bunch of emails and CSVs, your team can collaborate all of their security/compliance stuff in one place and do the tasks they’re assigned.
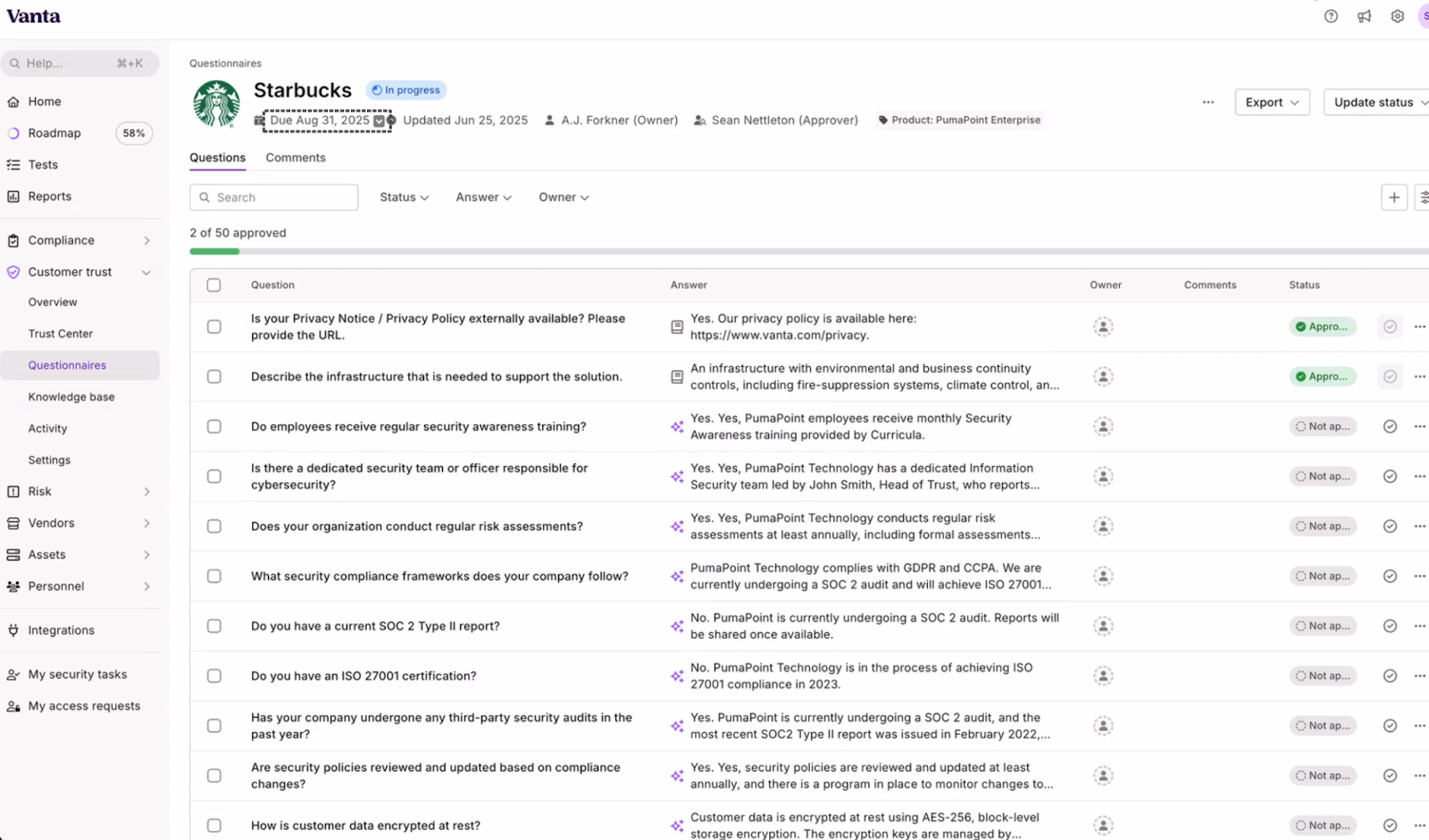
- Handling custom requests - Many customers ask for their own security questionnaires. Vanta utilizes AI that can use your internal data, reports, etc. to fill those questionnaires.
—
As with all companies, I think there are a few challenges that Vanta might encounter as it continues to grow.
Competition - If you’ve ever googled HITRUST…you know this space is cut throat. I assume there are streetfights and gang signs thrown at CISO conferences.
This space has gotten a lot of attention and funding in the last few years. Part of this is because there’s a lot of money spent on compliance, but also, the usable integrations with your software stack that automate the process lower the barriers of entry for new companies.
Vanta has historically focused on breadth of integration and simplicity of getting started (vs. customizability). They’re also pushing deeper into healthcare with their HITRUST partnership to gather your control scope and automate the submission to the myCSF application.
But I don’t think the opps are going to let them have this one easily.
The human component of security - There’s a lot of stuff you can automate from a security front, but there’s a lot of stuff that’s just…human. Do your employees know to not email their passwords to someone with a @proton.me email pretending to be from HR? Vanta can automate the security stuff that has integrations, but it’s up to the companies to make sure people are actually following the internal protocols.
And certain controls need humans to do stuff, but the extent you take it seriously is up to you. For example, take a tabletop incident response exercise. A team gathers in a room, walks through a “simulated breach” scenario, and hashes out who does what, when, and why. Then documents lessons learned and signs off on next steps. They get sweetgreen after.
Sure, you can script the scenario and record the meeting to make capturing documentation easy. But it requires people to sit down and do it. And how “seriously” you take that scenario is up to you - are you just checking the box or trying to build security into culture?
Another human component is the auditors who actually check if your company is doing what they say, but understand the difference between the spirit of a guideline and the specifics. One person told me they had this interaction with their auditor:
“Auditor: can you please provide evidence that all of your SQL databases are encrypted?
Me: We don't have any SQL databases!
Auditor: I still need evidence
Me: Well, I guess it's vacuously true
Auditor: …
Me: Spun up an empty RDS database and clicked the "encrypt" checkmark.”
Vanta has a network of audit partners they work with, but you can’t control everything.
The price of compliance - There’s a broader conversation beyond Vanta about “how much compliance should we require”. The reality is that increasing the compliance requirements and making them the norm means that smaller companies are less able to meet them. Compliance has a real cost - personnel hours, extra vendors and precautions, the literal cost of getting certifications, and the timelines required for monitoring.
If every vendor requires HITRUST certification before they work with them, then it basically means that no small companies will be able to participate. In healthcare, where the stakes are higher it also means security is front and center in the conversation. There’s some form of tradeoff between how strict we want security to be and how easy we want new entrants in healthcare.
Vanta can make the personnel hours part shorter, but that’s only one part of the conversation and cost that a company incurs. For healthcare, maybe this is the amount of security we should expect before companies operate in the space. But we have to acknowledge that there is a tradeoff.
Conclusion And Parting Thoughts
We can all say it - no one LOVES all the work required for compliance. If you do, it’s a beige flag.
Vanta is betting that they can make compliance increasingly more automated and help companies proactively build with compliance in mind.
Whichever route you choose, just don’t be the company that gets to the finish line of a deal and realizes they’re 3 months behind on their SOC 2 timelines. You’re going to make it worse for the rest of us. Plan your timelines early.
Thinkboi out,
Nikhil aka “2SOC Shakur”
Twitter: @nikillinit
IG: @outofpockethealth
Other posts: outofpocket.health/posts
--
{{sub-form}}
If you’re enjoying the newsletter, do me a solid and shoot this over to a friend or healthcare slack channel and tell them to sign up. The line between unemployment and founder of a startup is traction and whether your parents believe you have a job.
INTERLUDE - FEW COURSES STARTING VERY SOON!!
See All Courses →A reminder that there’s a few courses STARTING VERY SOON!!
LLMs in healthcare (starts 9/8) - We break down the basics of Large Language Models like chatGPT, talk about what they can and can’t do in healthcare, and go through some real-world examples + prototyping exercises.
Healthcare 101 (starts 9/22) - I’ll teach you and your team how healthcare works. How everyone makes money, the big laws to know, trends affecting payers/pharma/etc.
We’ll do group rates, custom workshops, etc. - email sales@outofpocket.health and we’ll send you details.
INTERLUDE - FEW COURSES STARTING VERY SOON!!
See All Courses →A reminder that there’s a few courses STARTING VERY SOON!! And it’s the final run for all of them (except healthcare 101).
LLMs in healthcare (starts 9/8) - We break down the basics of Large Language Models like chatGPT, talk about what they can and can’t do in healthcare, and go through some real-world examples + prototyping exercises.
Healthcare 101 (starts 9/22) - I’ll teach you and your team how healthcare works. How everyone makes money, the big laws to know, trends affecting payers/pharma/etc.
How to contract with Payers (starts 9/22) - We’ll teach you how to get in-network with payers, how to negotiate your rates, figure out your market, etc.
We’ll do group rates, custom workshops, etc. - email sales@outofpocket.health and we’ll send you details.
INTERLUDE - FEW COURSES STARTING VERY SOON!!
See All Courses →A reminder that there’s a few courses STARTING VERY SOON!! And it’s the final run for all of them (except healthcare 101).
LLMs in healthcare (starts 9/8) - We break down the basics of Large Language Models like chatGPT, talk about what they can and can’t do in healthcare, and go through some real-world examples + prototyping exercises.
Healthcare 101 (starts 9/22) - I’ll teach you and your team how healthcare works. How everyone makes money, the big laws to know, trends affecting payers/pharma/etc.
How to contract with Payers (starts 9/22) - We’ll teach you how to get in-network with payers, how to negotiate your rates, figure out your market, etc.
Selling to Health Systems (starts 10/6) - Hopefully this post explained the perils of selling point solutions to hospitals. We’ll teach you how to sell to hospitals the right way.
EHR Data 101 (starts 10/14) - Hands on, practical introduction to working with data from electronic health record (EHR) systems, analyzing it, speaking caringly to it, etc.
We’ll do group rates, custom workshops, etc. - email sales@outofpocket.health and we’ll send you details.
INTERLUDE - FEW COURSES STARTING VERY SOON!!
See All Courses →Our Healthcare 101 Learning Summit is in NY 1/29 - 1/30. If you or your team needs to get up to speed on healthcare quickly, you should come to this. We'll teach you everything you need to know about the different players in healthcare, how they make money, rules they need to abide by, etc.
Sign up closes on 1/21!!!
We’ll do group rates, custom workshops, etc. - email sales@outofpocket.health and we’ll send you details.

Interlude - Our 3 Events + LLMs in healthcare
See All Courses →We have 3 events this fall.
Data Camp sponsorships are already sold out! We have room for a handful of sponsors for our B2B Hackathon & for our OPS Conference both of which already have a full house of attendees.
If you want to connect with a packed, engaged healthcare audience, email sales@outofpocket.health for more details.







